Admin🔗
The Admin section provides high-level system configuration, user management, security, operational management tools, and settings.
VNFs🔗
The VNFs section manages virtual machine installations of the vNetC and SDLC, including the ACS, GuiA, SensAI, and Device Controllers.
vNetC Commander🔗
This section is composed of important processes working within the vNetC virtual machine. 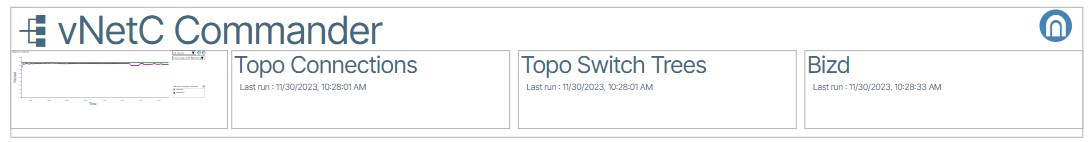
System Applications🔗
System Applications are:
- ACS
- DHCP Server
- GuiA
- SensAI
Installing System Applications🔗
- Go to Admin.
- Select VNFs.
- Click Add a System Application button (
 )
) 
- In the window that appears, click the desired System Application
 .
.
The example below demonstrates how to install GuiA; the steps are applicable to the other System Applications.
How to Install or Update GuiA🔗
GuiA stands for Graphic UI Acceleration and is a System Application that increases UI performance. To add GuiA to your application do the following:
- Go to Admin/VNFs (
 ) and navigate to the section of the window titled System Applications .
) and navigate to the section of the window titled System Applications . - Click the create button (
 )
)  .
. - Choose GuiA from the prompt
 .
. - In the window that appears, enable the application by clicking the enable button (
 )and fill out the fields with the relevant IP information.
)and fill out the fields with the relevant IP information. 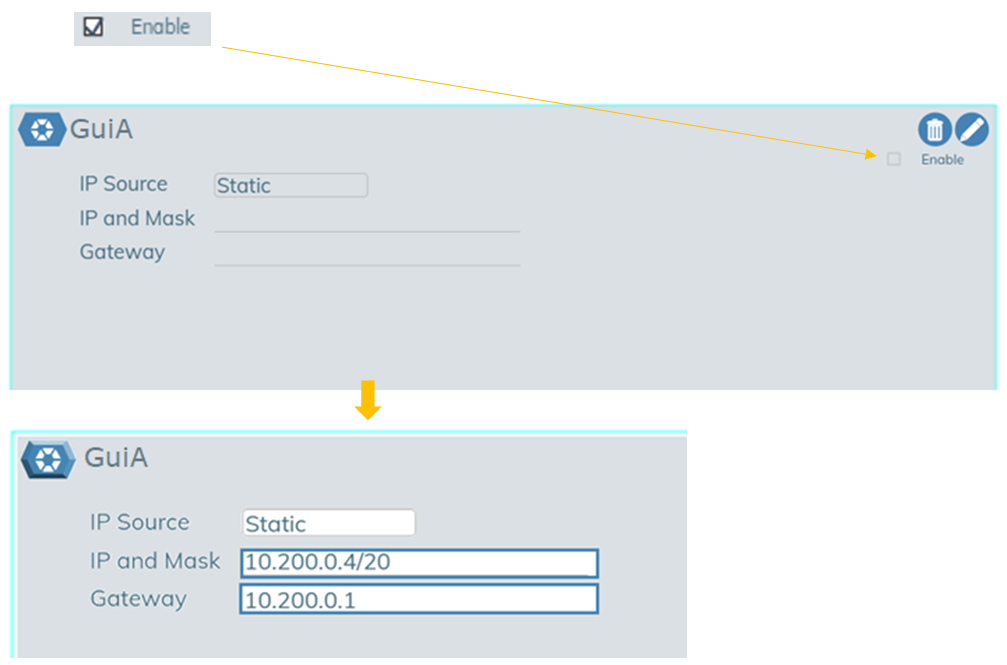
- Save your work by clicking the checkbox icon(
 ).
). - The yellow Status box text will read Awaiting Status. When it changes to Connected, the process is complete.
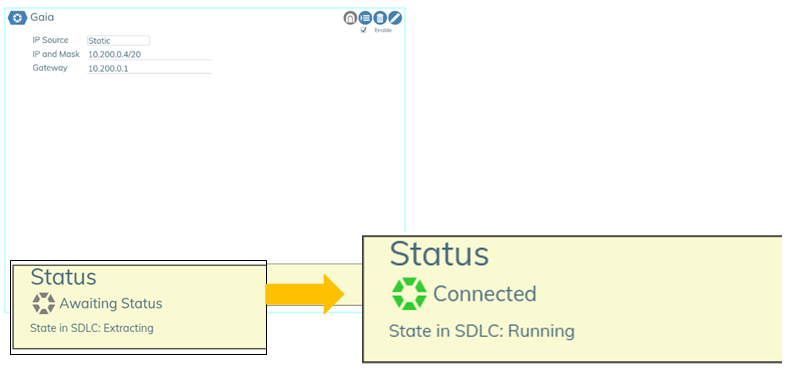
How to Install or Update SensAI🔗
SensAI is Verity's AI-powered messaging assistant. To add SensAI to your application do the following:
- Go to Administration/VNFs (
 ) and navigate to the section of the window titled System Applications (
) and navigate to the section of the window titled System Applications ( ).
). - Click the create button (
 )
)  .
. - Choose SensAI from the prompt
 .
. - In the window that appears, enable the application by clicking the enable checkbox (
 )and fill out the fields with the relevant IP information.
)and fill out the fields with the relevant IP information. 
- Save your work by clicking the check icon(
 ).
). - The yellow Status box text will read Awaiting Status. When it changes to Connected, the process is complete.

Together API Key integration for SensAI🔗
SensAI requires a valid TogetherAI API key via https://api.together.ai/ to run properly. The user will be asked to create an API-Key from their account at: https://api.together.ai/settings/api-keys.
To configure the system using your Together AI API key, follow these instructions:
Note
SensAI requires the Together.AI "meta-llama/Llama-3.3-70B-Instruct-Turbo" LLM Model.
- Open the VMware application that contains the Satori VM. Select the Satori VM and under the Virtual Machine column click Console/Open browser console.
- Login to Satori with your username and password.
- Run the setup application from the shell by typing
sudo ./satori_admin.shand pressingEnter. You will see the following interface:
****************************************
Welcome to the Satori Admin Menu
****************************************
Please choose an option:
1) setup
2) troubleshooting
#?
Select Setup
- When prompted with #?, choose: 1 for
setup. - Press Enter to confirm your selection
Note
- If you enter an invalid option, you'll see:
"Invalid option. Please select 1 or 2." - The menu will remain active, allowing you to make another selection
Press Enter to skip through each menu item until prompted for your Together AI API key.
Type or copy your TogetherAI API key and press Enter.
After submitting your Together AI API key type sudo reboot to reboot the VM. After the reboot, it takes about 3 minutes for the Docker containers to start up and to announce itself to the vNetC.
Licensing🔗
Licensing displays the license expiration date, support contact information, and reports on license and physical port usage.
Users🔗
Users provides tools for authentication, user settings, and role assignment.
Roles🔗
The Roles settings can be accessed via Admin/User Roles. This lets users assign feature access to roles. To access this feature you must first enable Granular Permissions in feature flags..
The Roles window contains a collection of checkboxes with each user role listed as a column item and each feature listed as a row item. You enable and disable checkboxes to determine what features are accessible to each role.
Verity supports role based access (RBAC) permissions scheme to partition the various workflows to operational personnel.
| Permission | Parameters | Role |
|---|---|---|
| [DEV] Device Management | Add device controller, Edit device controller, Delete device controller, Swap switchpoints, Set read only mode, Capture device snapshot, Trigger a full device rescan by ACS, Open a remote access tunnel, Reboot switch, Mark device out of service. | Device Operations |
| [NW] Network | Edit POD name, Add a new preprovisioned switch Designate LAN TORs (Management Network), Lock switch Edit site, Create switch pairs, Create a static connection, Site Settings (DHCP snooping, Aggressive Reporting, CRC Failure Threshold) , Underlay Fabric Configuration | Network Operations |
| [SEP] Switch Endpoint | Edit Switch Name and type (spine/leaf) Delete Switch Edit switch Note, Port Provisioning | Day-Day Service Management |
| [BP] Base Provisioning | Manage Tenants, Gateways, LAGS, Route map assignments | Infrastructure |
| [GBL] Globals | Manage badges, RADIUS servers for 802.1x | Security |
| [IE] Import | Import snapshots, Clear system | Global Provisioning |
| [ADM] Admin | The Admin Role grants access to edit all features in the GUI | User Administration |
| [SVC] Services | Manage services, Change assigned tenant | Service Creator |
| [SET] Sets | Manage Firmware Update Sets | Software Manager |
| [VIEW] Views | Manage Views | Monitoring |
Assigning Users to Roles in Accounts🔗
In Admin/User Accounts, each user is assigned a role.
- From the Admin window select the Users Accounts item box
 .
. - In the window that appears, click the Access Level menu item twice for the chosen user.
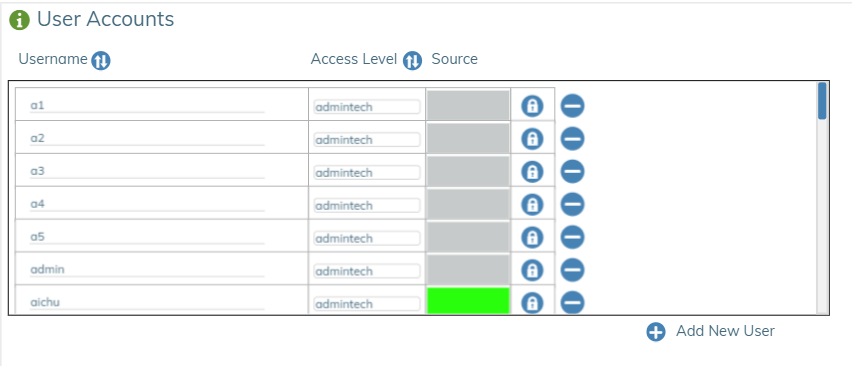 You can also select the edit icon (
You can also select the edit icon ( ) in the upper right corner of the User Accounts window to edit the page.
) in the upper right corner of the User Accounts window to edit the page. - Choose the Username you want to change and set the Access Level to the desired role.
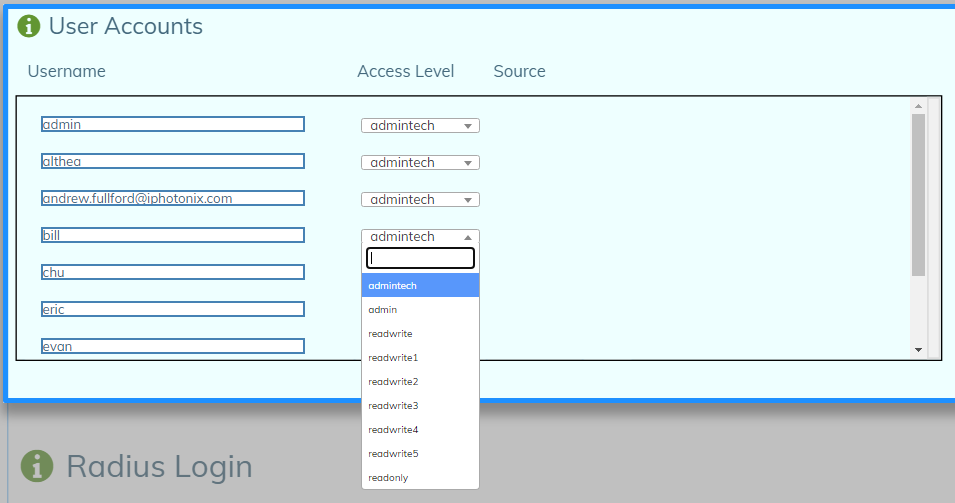
- To complete the process, click the checkmark (
 ) in the upper right corner of the User Accounts window to save your work.
) in the upper right corner of the User Accounts window to save your work.
User RADIUS Logins🔗
Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA or Triple A) management for users who connect and use a network service. RADIUS is a client/server protocol that runs in the application layer and can use either TCP or UDP as transport. The devices associated with Endpoints control access to a network as they contain a RADIUS client component that communicates with the RADIUS server. RADIUS is often the back end of choice for 802.1X authentication as well.
To access the RADIUS Logins settings:
Navigate to Admin and under the Users column select User Radius Logins
 .
.
RADIUS Login Secure Deployments🔗
The Verity platform provides the option for RADIUS integration iVN-Authorization/Server IP/Port/Shared secret are required inputs. User permission level will be passed down according to the following levels:
Vendor IDs are assigned by IANA
| VENDOR | iPhotonix | 49683 |
RADIUS dictionary for Verity remote authentication provides the initial authorization level. Once authenticated, accounts are automatically created and updated with the iVN-Auth level. The "superuser" user does not actually exist within Verity, it is mapped to (same as) the "admin" user. The "authenticated" value indicates that the user is authenticated but that the authorization is based on internal records as managed by the Verity Admin page. The initial level is readonly. An authentication returned with no iVN-Auth entry will be ignored. Only the first iVN-Auth will be honored.
| ATTRIBUTE | iVN-Auth | |
|---|---|---|
| VALUE | iVN-Auth | superuser |
| VALUE | iVN-Auth | admin |
| VALUE | iVN-Auth | readwrite |
| VALUE | iVN-Auth | readonly |
| VALUE | iVN-Auth | authenticated |
Optional authorization modifier
This instructs the Verity Web UI to modify the operations and results available to the user. For example, the value "tech" modifies the web behavior for "admin" and "superusers" to include more technically-oriented features.
| ATTRIBUTE | iVN-Auth-Modifier | string |
|---|---|---|
| VALUE | iVN-Auth-Modifier | tech |
Certificates🔗
Certificates manages the import and revocation of application certificates. This is where you work with SSL certificates, certificate chains and certificate revocations.
How to Import Certificates🔗
To import a Certificate, go to the Admin section and select Certificates ( ).
).
Double-click the tile that describes the certificate you want to upload. You can either drag the certificate to the drag and drop section or click the browse button and select your certificate file to upload it  .
.
vNetC Server Certificate🔗
For the vNetC Server Certificate panel, certificate files must be in PEM format. The vNetC Server Certificate should include
- Private Key File
- Certificate File
- Optional CA Intermediate Certificate
These should all be in PEM format, concatenated in that order. The CA Root Certificate should not be included.
Once uploaded, the vNetC Server Certificate is automatically added to the backend web path. Although this does reconfigure the backend process, this is done so that new connections will be handled using the new certificate but old connections will continue the operate as before, so there is no outage of the web service during a certificate update.
Information
Verity can be configured to support client certificate authentication. This operates in a "lockdown" mode that meets US DoD requirements. It does impose strict access requirements on all transports in the systems and demands client certificates for all users, devices, and external application access.
Software🔗
The Software section controls software lifecycle management including vNetC platform packages, hardware-specific firmware images, bundled image packages, configuration file management, and application package deployment.
External🔗
External integrates with external monitoring and management systems and automates database backup configurations.
DB Backups🔗
How to Automate DB Backups🔗
- Select Admin/DB Backup from the Main Navigation Bar
 .
. -
Enter the required information:
- BWLimit(kbps): Bandwidth Limit
- User: Username on the remove server
- Server: Remote server name (can be IP address or hostname)
- Port: IP port of the remote server
- Filepath: Path on the remote server
-
Enable the Enabled and Host Subdir boxes
- Once Enabled, click the Auth Key button to copy the authorization key.

- In the the database server, paste the key into: .ssh/authorized_keys
- Save
Branding🔗
Branding customizes the user interface with white-label options, including the login banner, top navigation logo, browser favicon, splash screen, and general application settings.
Network🔗
Network configures system-wide network behavior, management connectivity, WAN routing, and optional feature toggles.
Site Settings🔗
Enable DHCP Snooping🔗
This feature enables DHCP Snooping.
DHCP Snooping is a security feature that helps protect against rogue DHCP servers, and along with the IP Source Guard capability, it protects against man-in-the-middle attacks or IP address conflicts. Rogue DHCP servers can assign incorrect IP addresses to devices, potentially leading to network downtime or security vulnerabilities.
The Enable DHCP Snooping feature is used to learn IP addresses offered to clients on ‘Untrusted Ports’. DHCP Snooping protects your network by monitoring DHCP traffic and associating MAC addresses with assigned IP addresses on untrusted ports. As a side effect, only ports designated as trusted are allowed to forward DHCP OFFER messages. This is independent of the Verity Service feature, which blocks DHCP Servers.
When the system is in a secure ‘lock down’ mode, ‘IP source guard’ is enabled. All traffic from client devices that do not match the learned IP address and MAC address bindings is blocked. IP addresses can also be set statically.
Aggressive Reporting🔗
This setting decreases the interval (and increases the polling rate) of switch controllers to 5 seconds.
CRC Failure Threshold🔗
The maximum number of CRC errors per second that will trigger automatic disabling of the port if it's part of a Link Aggregation Group (LAG).
DSCP to TC Map🔗
DSCP to TC Map is a translation table that converts quality-of-service markings between two different systems. This feature maps incoming DSCP priority markings (0-63) to internal Traffic Class queues (0-7) to ensure high-priority traffic like voice and video receives proper handling.
Click the Priority numbers below the DSCP numbers ( ) to choose the range of numbers to set (
) to choose the range of numbers to set ( ).
).
Feature Flag🔗
Feature flags are used to enable or disable visibility of options in the UI and other system wide behaviors. Please consult with BE Networks regarding the usage of these settings beyond the defaults that are set upon installation.
Admin Settings🔗
Admin Settings is accessed from Admin/Admin Settings and lets you configure the following:
- vNetc Address on Management VLAN
- Permissible IP Address Ranges on Managed Devices
- Customized Download Address/FQDN
Routing🔗
Routing includes the following WAN IP information.
- Hostname (fully qualified domain name)
- RAT Port Range
- WAN IP Source (DHCP or Static)
- WAN Default Route
- WAN IP Address
- DNS Server

