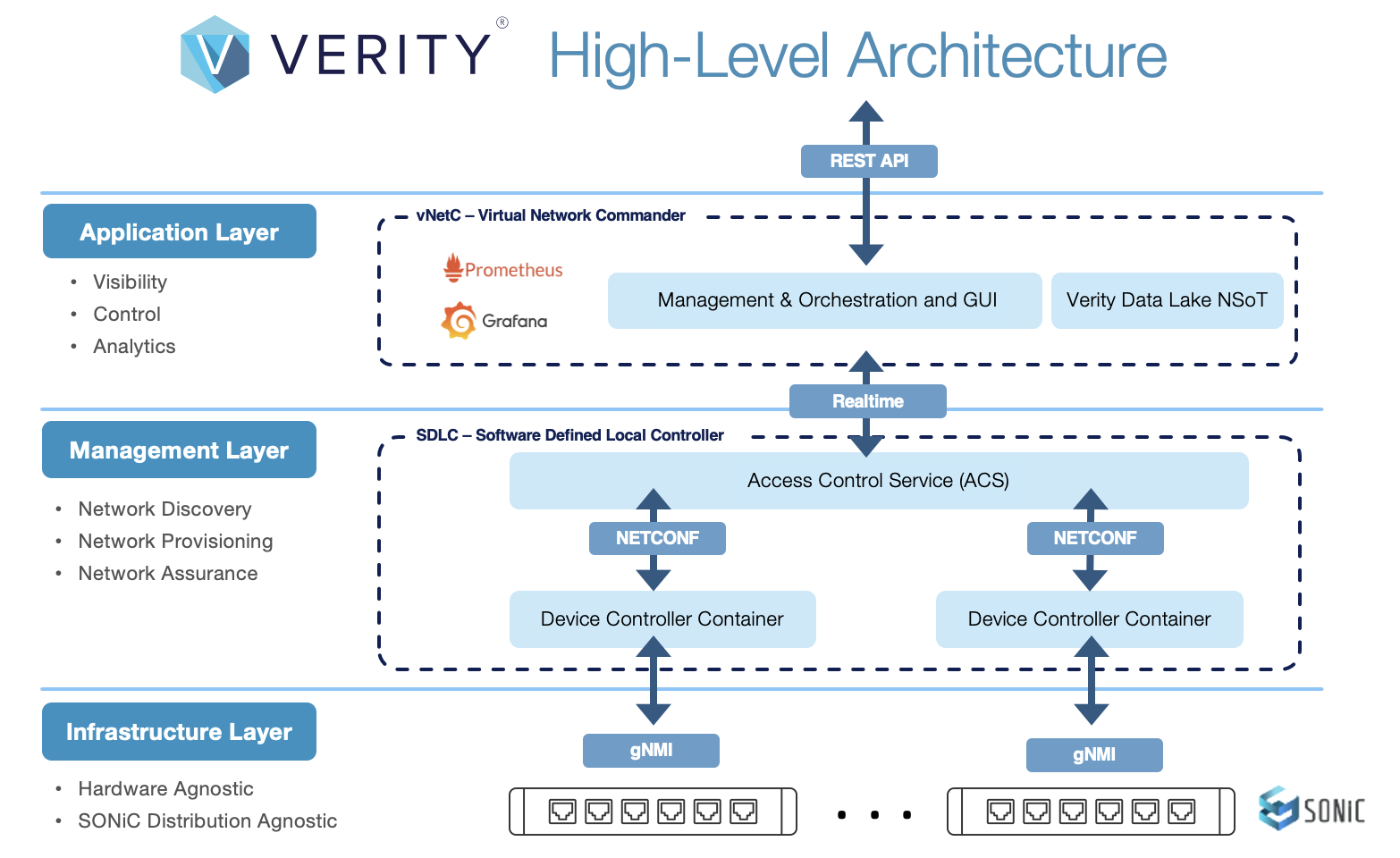
Verity Components🔗
Software Defined Local Controller (SDLC)🔗
The SDLC hosts the various containers used for device communications and other system functions. This is a Linux Virtual Machine that is installed during the initial deployment of Verity. This VM hosts the following containers:
-
ACS (Access Communication Server) provides a scalable message interface between vNETC and all managed devices. ACS controls how the devices are programmed from the UI to the Device Controllers.
-
GuiA (UI Acceleration) is a system application that increases UI performance. Only one GuiA can be used per SDLC. This is the UI backend that takes the inputs from the user through the UI and codes it so that the ACS can translate to the Device Controllers and manage the devices.
-
Device Controllers are used to create the interface between the Verity application and the switch device. Based on the LLDP capabilities of the switch, it can be automatically discovered in the network topology, or it can be statically located.
Virtual Network Commander🔗
The vNETc hosts database services, a UI HTTPS server, the optional DHCP server, and the BizD application which translates user intent to actual network state. The Web Server also works with the GuiA services on the SDLC’s to be able to draw and reflect in real-time what is happening to the devices and configurations.
Monitoring🔗
The Monitoring VM hosts multiple containers to provide enahnced and detailed monitoring to Verity. The Monitoring VM gets telemetry, log, and other metric data for the managed devices in Verity. This is a Linux Virtual machine that is installed during the initial deployment of Verity.
Hardware Devices🔗
These are the physical devices that Verity works with. In Verity, these are either managed devices or unmanaged devices. Managed Devices are ones that are known to Verity and mapped to SDLC Device Controllers and the system is and managing them. Unmanaged Devices are devices that Verity detects on active links but are not managed like servers and/or switches. These devices are typically servers or other switches that are not included in the Verity Inventory and the system is not aware of how to manage them. Firewall’s and Load Balancers also fall into this category.
Management Network🔗
The backend L2 network that is managed by Verity. For Verity to function correctly, it needs to be able to access the managed devices via their management interface. Verity uses SSH, gNMI, SNMP and other protocols to manage devices in the OOB management network. During initial deployment, Verity can deploy and program the management network and automatically configure the attached switches, as well as inventory and detail how and where they are connected to the Management Switch(es).