Provisioning🔗
Templates > Templates > Provisioning
The provisioning section of the Verity GUI is designed to help users configure and prepare the network and its components (such as services, endpoints, devices, etc.) before, during, or after the physical installation and power-up of the network infrastructure.
The Provisioning panes have multiple zoom levels. The first level shows the count of template objects with a diagram depicting their relationships. Any objects that are changed once they are in use are automatically updated everywhere they are referenced. For example, if an object is renamed, all references to it are also automatically renamed. Additionally, if a single parameter is modified, all objects inheriting that parameter are also updated. This is a powerful feature, and the user is given a pop up indicating the count of objects affected throughout the system.
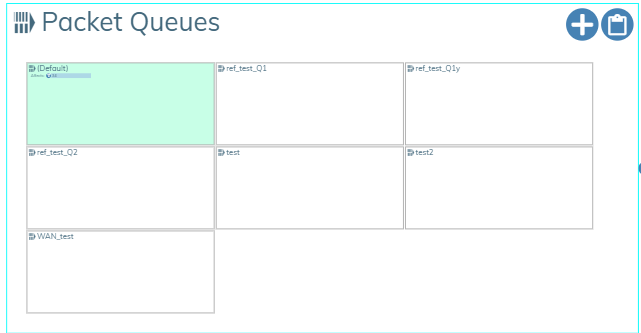
All provisioning profiles contain a non-editable instance named Default shown with a green background.
Packet Queuing🔗
This feature lets you set the priority for packets depending on bandwidth.
You can use an existing Packet Queue or create a new one using the  icon.
icon.
The window that appears lets you make your changes. Here you set the priority for p-bits and set the bandwidth (BW) for each queue as a percentage. The percentage is the maximum average percentage of the port output bandwidth that packets in that queue will be allowed to consume. The value cannot exceed 100 and a value of 0 means no limit is set.
MAC Filters🔗
This is a feature that allows you to filter which devices can use a service based on MAC Address. MAC Filters consists of MAC Addresses and Hexadecimal Masks. When a MAC Filter is assigned to an Eth Port Profile, the Services assigned to that Eth Port Profile can be translated to the same VLAN.
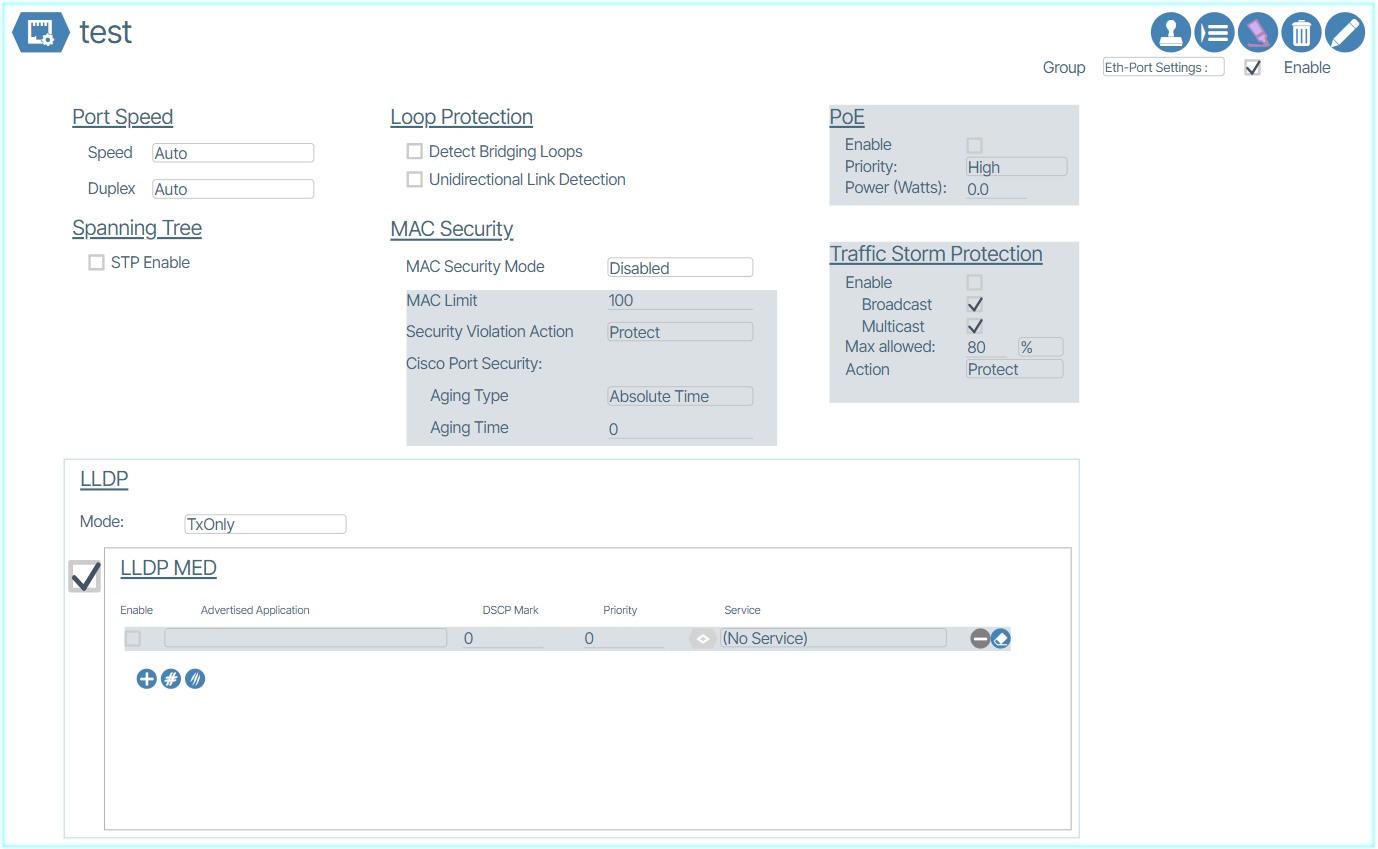
Ethernet Port Settings🔗
This window is used to set Ethernet Port speeds, per Port PoE settings and client device LLDP handling.
The following figure shows the detail within an Ethernet Port Settings dialog box:
Unidirectional Link Detection (UDLD)🔗
Unidirectional Link Detection (UDLD) is a Cisco-developed layer 2 protocol that is used to determine the physical condition of a link. Its purpose is to identify and address any problems that may be caused by Unidirectional Links.
Unidirectional Link Detection is available in Eth-Port Settings under Loop Protection.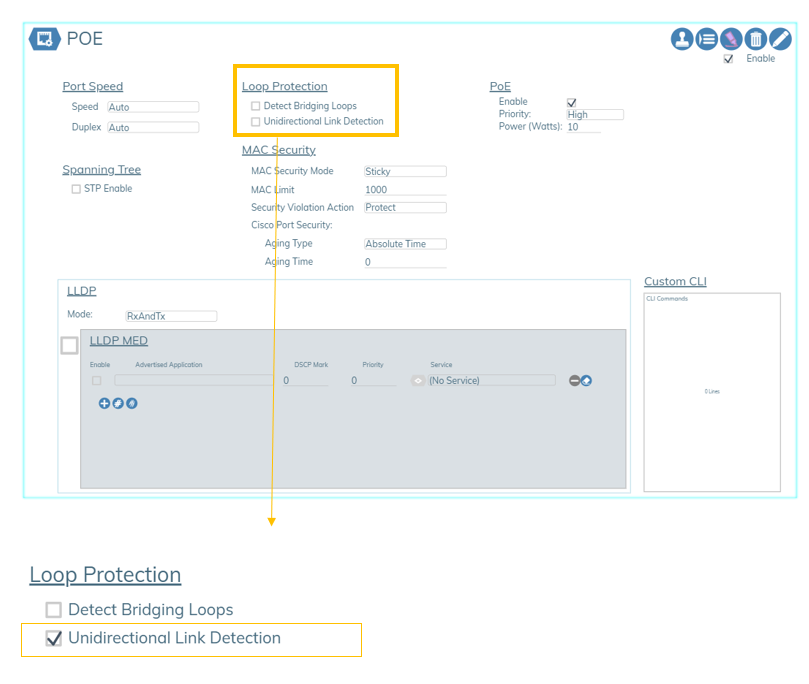
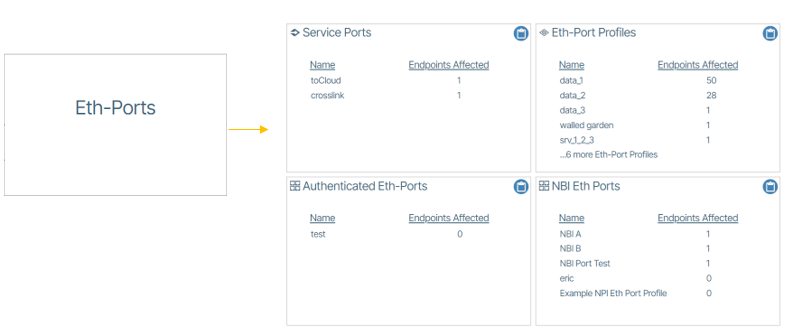
Eth-Ports🔗
Eth-Port Profiles🔗
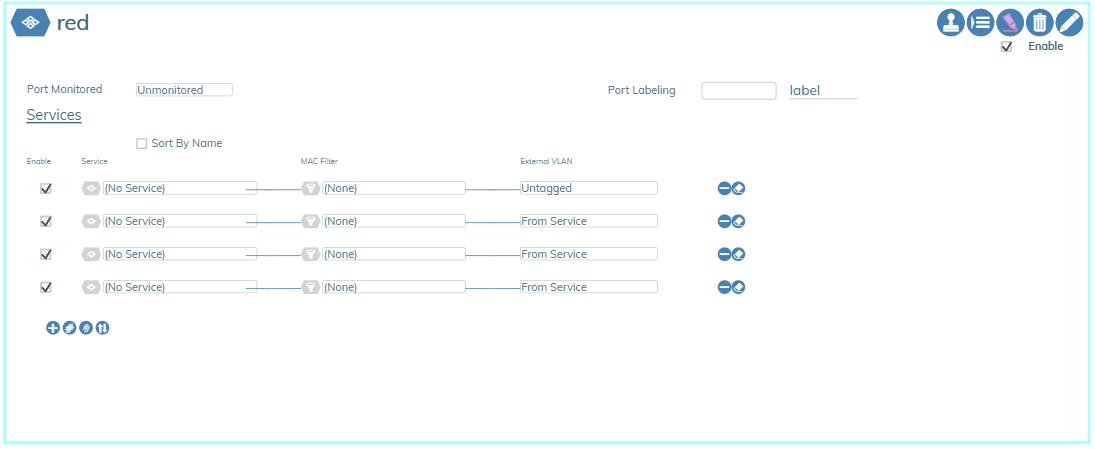
Ethernet-Profiles provides the definitions for each use case of Ethernet port usage within the network. It is a packaging of up to 25 services that are served by this port type combined with the Ethernet Port Settings and MAC Filters. Examples of external VLAN handling are shown in the example above.
Enabling the “Monitored Port” option allows the service status of ports using this profile to be included in system alert reports.
How to Create an Eth-Port Profile Assigning Services to an Eth-Port Profile
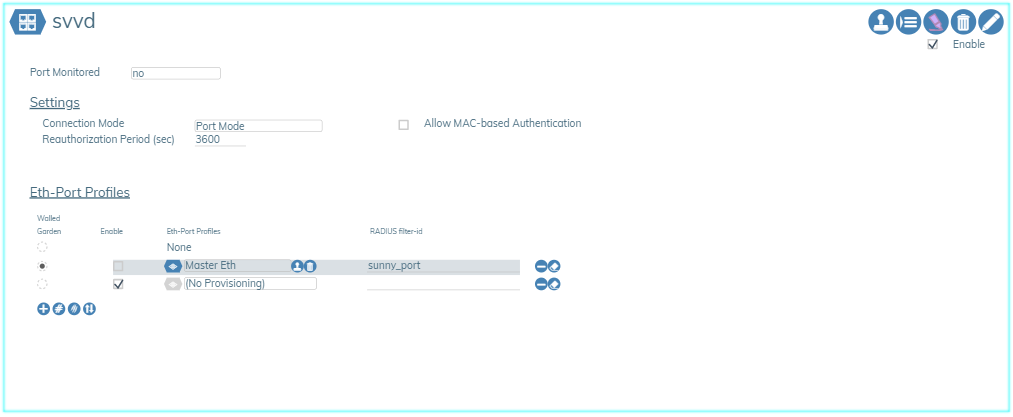
Authenticated Eth Ports🔗
An Authenticated Ethernet Port profile is comprised of a list of Ethernet Port Profiles. This feature is used on networks that employ user detection and authentication via 801.1x protocols. The Managed End Device communicates to connected user devices as they connect to the assigned port, and relay control messages to a Radius server, to validate the user and select and enable the appropriate Ethernet Port Profile on the port.
An example is shown below.
The “Settings” section allows a change in the connection mode the user device contains, ranging from 3 different modes. Port Mode, which is the standard mode, Single Client Mode which disables traffic from a second client, only allowing the authenticated client’s traffic to pass. Lastly, Multiple Client Mode which allows multiple clients’ traffic to pass.
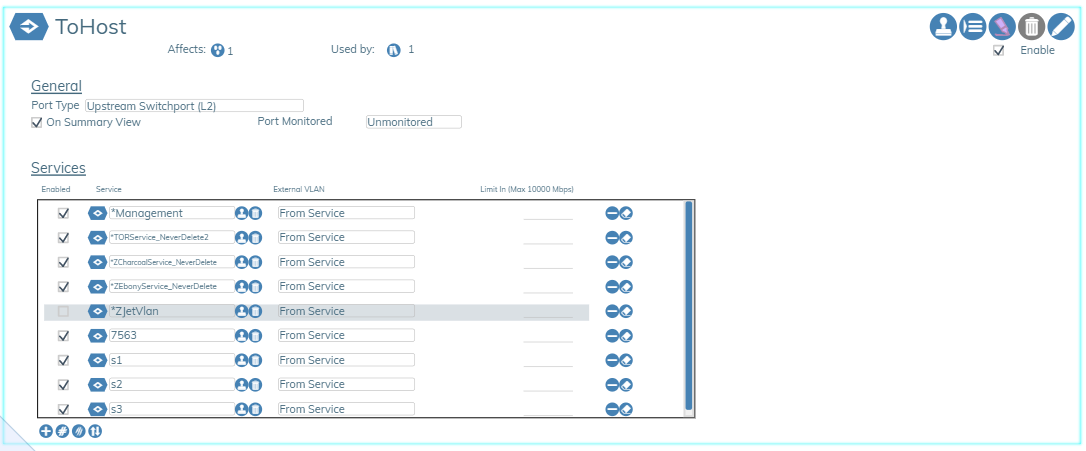
Service Port Profiles🔗
Service Port Profiles are normally assigned to links or LAGs connected to the TOR switch of the network. The user can edit the maximum downstream rate allowed on a per service basis. Other parameters such as spanning tree and port monitoring are set on the physical link.
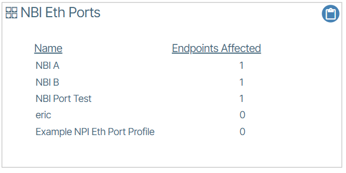
NBI Eth Ports🔗
NBI Port Access Control is a configurable UI feature that administrators apply to selected ports. It grants a client of the API access to the specified ports, enabling it to retrieve MAC addresses connected to those ports and control the set of services allowed on said port(s). The API utilizes a Representational State Transfer (REST) style interface over HTTPS.
The current port state is accessible to any user via the API. Only users with read-write and admin-level privileges can modify a port's configuration.
Device Voice Settings🔗
Device Voice Settings are the settings used for configuring the VOIP stack on the ONT. Parameters that are generic to each device (where all ports on a device must share) are shown in the following example. There are two formats for the dialogue box based on whether SIP or MGCP is used.
Device Settings🔗
LED Control time is a parameter that defines the number of seconds the LEDs will illuminate after a state change before extinguishing. This is used, for example, in hospitality installations to prevent blinking lights from disturbing a hotel client. The value of “0” disables the feature and allows the LEDs to operate normally.
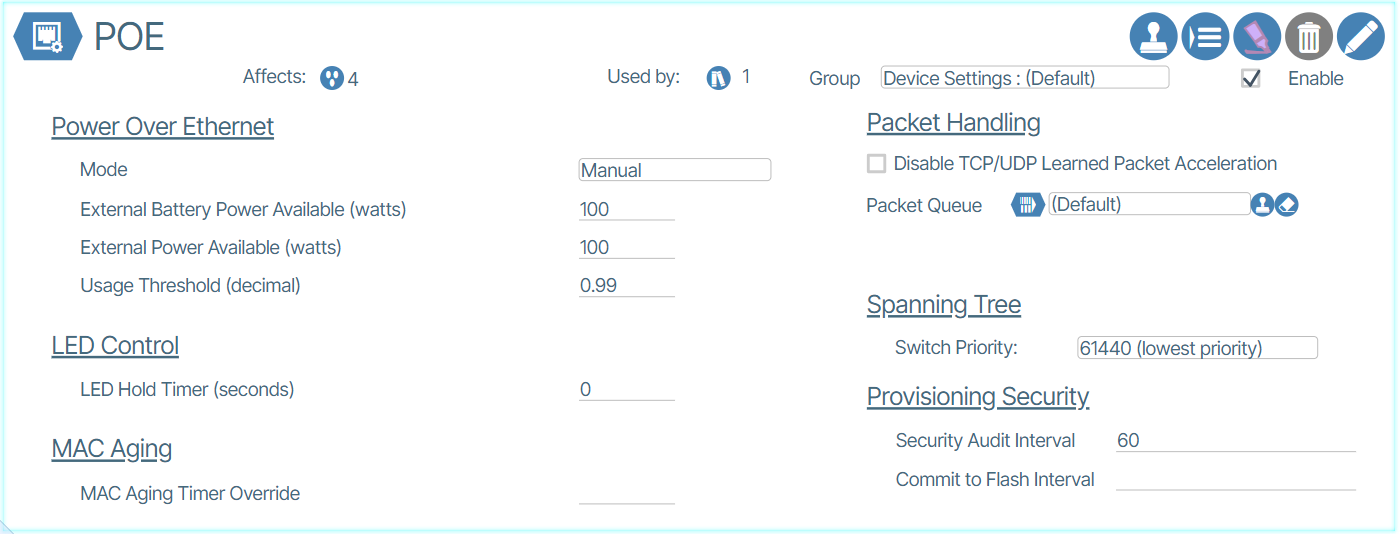
Power over Ethernet settings are used to set capacities of specific hardware devices that provide this feature.
Mode:
Automatic – The endpoint hardware or ONT handles all PoE automatically. No provisioning from the orchestration platform with regards to PoE will be used. This works for most cases.
Manual – Power allocation and port priority are provisioned by Verity. This is for more complex PoE scenarios.
External Battery Power Available: When the ONT is connected to an external battery backup, this is the maximum amount of power that the ONT should use to power PoE devices. This can be used to force low priority ports off when power is lost to preserve battery for higher priority ports.
External Power Available: Enter the power capability of the power supply powering the ONT.
Usage Threshold: Percent for comparing the currently consumed power to the allocated power. If the percentage of consumed power over allocated power is over the usage threshold, a fault condition is reported and logged.
Provisioning Security🔗
This functionality encompasses security audit interval configurations that are individually applied to each switch.
Security Audit Interval🔗
The frequency, measured in minutes, at which the Switch running configuration is reread and compared to expected values. If left blank, the audit will never be executed.
Commit to Flash Interval🔗
The frequency, measured in minutes, at which the Switch configuration is saved to flash. If the value is empty, the system will never commit to flash.
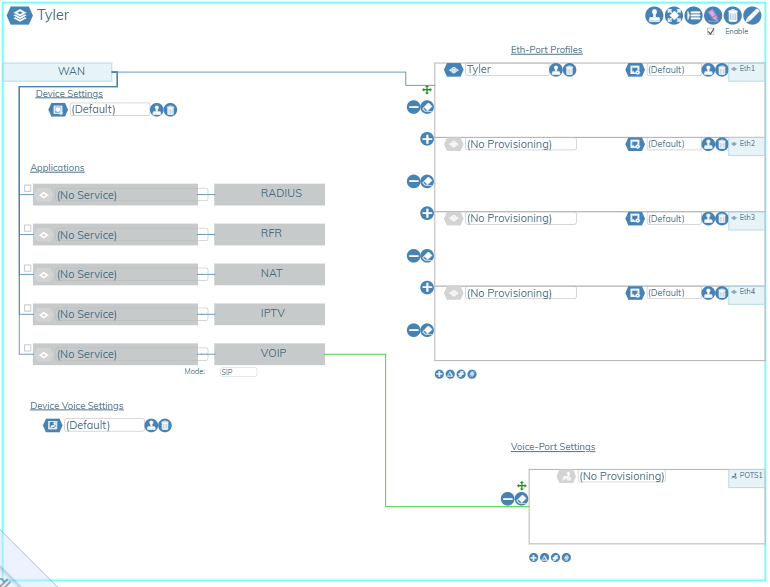
Endpoint Bundles🔗
A Bundle is the group of template settings used to configure, program and set the state of a switch or ONT. A GUI instance can have many bundles (hundreds) each for a different switch. Ideally, you will have 1 bundle for many ONT's. All devices require a bundle assignment (and an endpoint). Bundle assignment is part of the provisioning process.
- A collection of VLAN settings compose a Service.
- A collection of Services compose an Eth-Port Profile.
- A collection of Eth-Port Profiles compose a Bundle.
- A Bundle is a collection of settings transmitted to different Endpoints.
The following figure shows the detail within a Bundle dialog box used to combine the device settings, Ethernet Port Profiles/Dynamic Policies, and Residential Applications. The number of Ethernet lines represented can be adjusted with the “+” and “-” icons, when not in edit mode. There are also buttons for removing, adding, and swapping multiple Eth-Ports.
To get the most effective use of bundles, it is highly recommended to have a deliberate plan for network installation that allows for consistent port usage across the network. The more devices that can be managed with fewer bundles, makes provisioning and operations of the network much more efficient.